Uber awards investigator $10,000 for reportage security hole

Uber awards investigator $10,000 for reportage security hole
Uber has awarded an investigator $10,000 for locating a login bypass bug that associate assaulter might have wont to compromise the company’s internal network. On May 4th, Finnish investigator Jouko Pynnönen, UN agency works for the protection company Klikki Oy, submitted a report back to Uber’s bug bounty program hosted on HackerOne.
He determined however many *.uber.com websites do not use the WordPress login. Instead, they accept OneLogin, a supplier of single sign-on (SSO) and identity management services for cloud-based applications that use SAML and OpenID further as alternative formats and standards.
Uber awarded Finnish security investigator Jouko Pynnönen $10,000 for locating the flaw last month, equalling the very best bounty the corporate has paid out since it launched the program earlier this year. The exploit had 2 components, per Pynnönen, one that allowed him to bypass the system Uber uses for worker authentication, OneLogin, associated another that might have let an assaulter compromise Uber’s internal network, hosted on Atlassian’s Confluence collaboration code. Pynnönen, UN agency works for the firm Klikki Oy, told Threatpost on Tuesday that the login bug he found may well be wont to compromise a server that uses WordPress – like Uber’s PR website, newsroom.uber.com.
See additional at Uber Pays investigator $10K for Login Bypass Exploit https://wp.me/p3AjUX-uPy
According to the investigator, the WordPress plugin shipped by OneLogin contained a bug that allowed associate assaulter the flexibility to provide any username, email address, name, or role they wished. “If the username doesn’t exist already within the WordPress info, then the plugin can produce a brand new user,” Pynnönen wrote in his summary of the bug on HackerOne. On one website, eng.uber.com, he was able to produce a “Subscriber” account, whereas, on another, the newsroom.uber.com site, he was able to produce associate “Administrator” account, just by approximation the role’s name.
After he had gained administrator privileges on the Newsroom web site, he discovered that he’d be able to persist and attack the interior web site in addition, since the majority of the pages thereon internal web site, team.uberinternal.com, check with a script hosted on the Newsroom web site. The second a part of Pynnönen ’s vulnerability hinges on the flexibility to switch that JavaScript file, adrum.js, to compromise Uber’s internal network. per the man of science, Associate in Nursing wrongdoer might have achieved remote code execution via the compromised web site, as a result of JavaScript will be injected from the Newsroom web site into the Confluence atmosphere.
Pynnönen delineates a particular example during which when it’s loaded, Associate in Nursing add-on/plugin containing code can be put in, and successively a backdoor servlet can be created. Uber was fast to handle the problems – fixing them each during a day – and acknowledged Pynnonen’s work by satisfying him with the company’s most bounty. The high payout was because of the enchained JavaScript supply, one thing Uber admits “elevates the impact” of the bug. Pynnönen in-camera reported the problems at the start of could, however, the corresponding bug reports didn’t go public on HackerOne till Mon. it absolutely was the second time Pynnönen has rewarded a $10,000 bounty this year for deed an essential security bug. In January, Yahoo disclosed that it had patched an essential vulnerability in its communication the previous month that Pynnönen discovered that might have given attackers complete management of a user’s account.
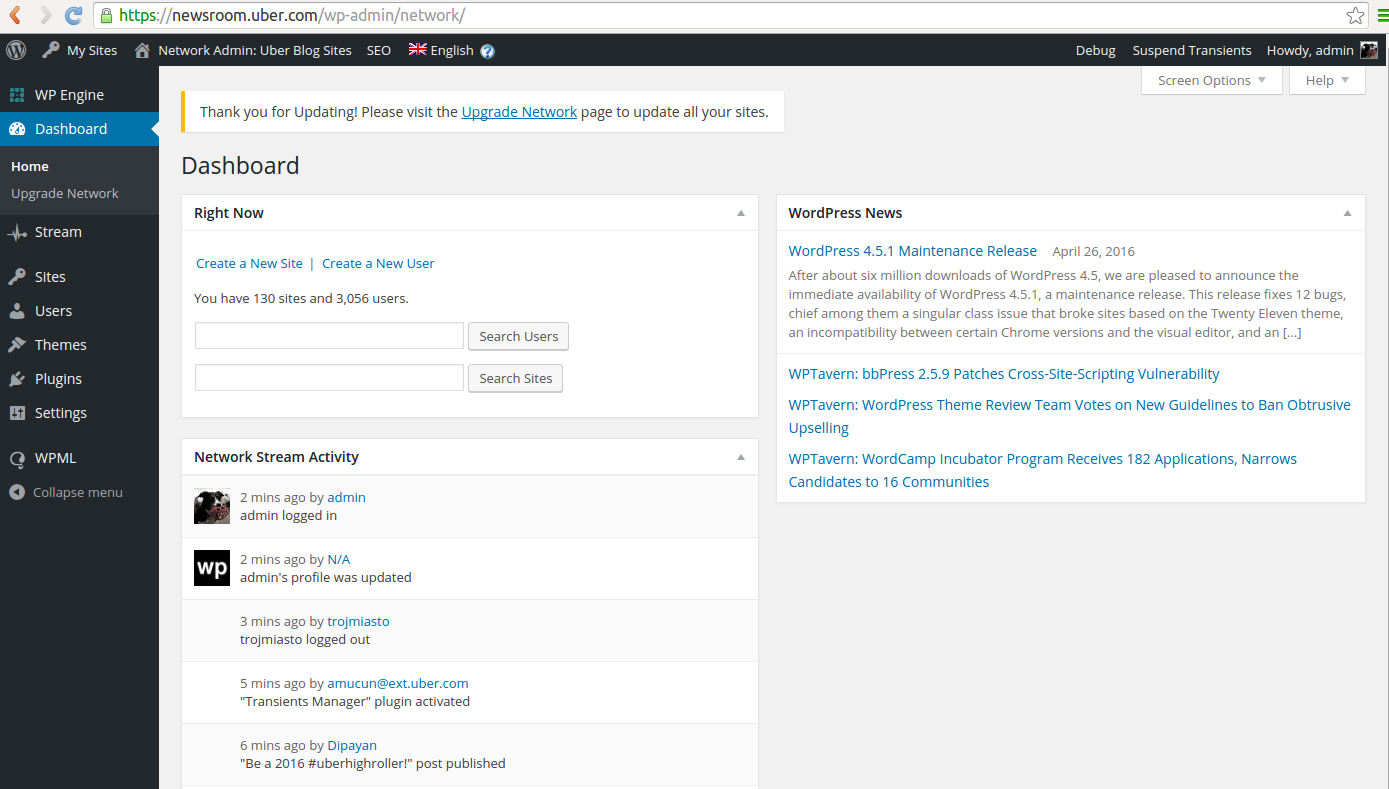
 Uber’s bug bounty program got off the bottom and graduated from non-public beta mode in March however thus far the corporate had solely awarded $10,000 to a man of science on one occasion. In March, shortly when the program’s origination, a man of science World Health Organization goes by the handle Orange discovered an overseas code execution vulnerability in its rider web site. Pynnönen has been good at finding bugs that have an effect on the ride-sharing app since the program debuted. He’s filed thirteen bug reports, primarily RCE, CSRF, XSS, and SQL injection vulnerabilities that have an effect on WordPress parts employed by the service, and is one among the highest reporters on the company’s HackerOne page.
Uber’s bug bounty program got off the bottom and graduated from non-public beta mode in March however thus far the corporate had solely awarded $10,000 to a man of science on one occasion. In March, shortly when the program’s origination, a man of science World Health Organization goes by the handle Orange discovered an overseas code execution vulnerability in its rider web site. Pynnönen has been good at finding bugs that have an effect on the ride-sharing app since the program debuted. He’s filed thirteen bug reports, primarily RCE, CSRF, XSS, and SQL injection vulnerabilities that have an effect on WordPress parts employed by the service, and is one among the highest reporters on the company’s HackerOne page.
See a lot of at Uber Pays man of science $10K for Login Bypass Exploit https://wp.me/p3AjUX-uPy
