Hackers attack via File transfer, XSS, and SQLi Bugs on Websites

Hackers attack via File transfer, XSS, and SQLi Bugs on Websites
It’s not news any longer that hackers wish to target WordPress sites, however, a recent report from Check purpose will facilitate some webmasters get AN insight into however they operate. The security firm analyzed mensuration knowledge from its security product and checked out attacks against WordPress plugins and themes alike. What the corporate discovered is that crooks wish to launch slow-and-low machine-driven attacks through that they take a look at websites for renowned vulnerabilities.
Attackers use machine-driven scripts to scan WordPress sites for vulnerabilities
Check purpose says it detected machine-driven scripts that sent out on the average 5 attacks per minute against WordPress sites. These attacks were nothing over POST and find requests, that checked if sure files and ways were prone to exploit payloads.
The crooks ne’er exploited these security weaknesses once they discovered them, however, they used the data to make a security standing report, that they used at a later purpose to compromise the positioning. In most cases, Check purpose says that crooks infected sites with malicious redirects, causing the guests to use kit landing pages, like those for Angler.
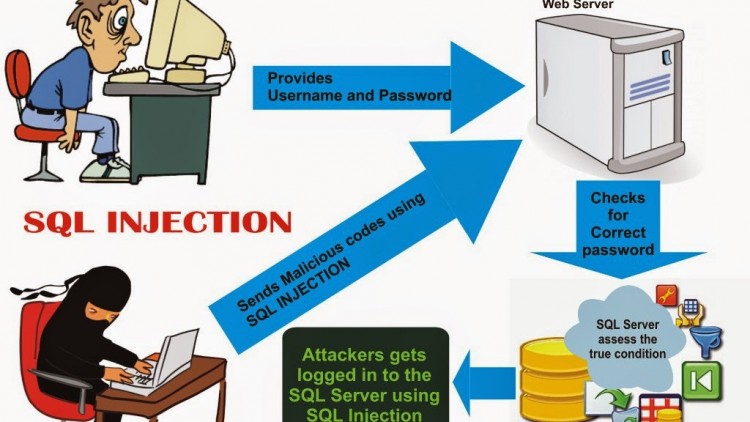
The security vendor says that, in most cases, the crooks leveraged File transfer vulnerabilities to compromise the websites. Check purpose explains it found File transfer vulnerabilities leveraged in twenty-four p.c of all the detected attacks. the remainder of the list goes as follows: Cross-Site Scripting (XSS) bugs – seventeen p.c; SQL injection (SQLi) flaws – fifteen percent; and Remote Code Execution (RCE) – eleven percent.
RevSlider remains a tangle for WordPress homeowners
Check purpose researchers additionally discovered that crooks did not care if the vulnerability was in an exceedingly theme or plugin, making an attempt to use each regardless. In terms of the foremost attacked plugin, in keeping with Check Point’s statistics, Revolution Slider (also called RevSlider) accounted for forty-eight p.c of all attacks. in an exceedingly distant second came the WP conference and Inbound selling plugins with six p.c every.
For themes, the statistics weren’t therefore decisive. Check purpose says the overwhelming majority of the attacks unfold against the Infocus2, Fusion, Awake, DejaVu, and Construct themes, with terribly little variations between them.
Last week, Sucuri revealed a comprehensive report on the state of net security, that additionally enclosed insights into WordPress exploits. you may wish to require a glance at that report moreover since it’s supported a distinct set of mensuration knowledge.
