Phases of Secure SDLC Software Development Life Cycle
The smart approach to creating secure software is Secure SDLC or Software Development Lifecycle. Instead of creating software and then testing it for vulnerabilities, it is better to create it with an emphasis on security.
What is Secure SDLC?
In a broader sense, a Secure SDLC is a process of integrating security testing and other measures in the existing software development lifecycle. This can include:
- Writing security requirements along with functional requirements.
- Performing architecture analysis.
- Using open-source components with no known security vulnerabilities.
- Testing the software at every stage and preventing vulnerabilities/threats from being carried forward.
Why Secure SDLC is Important?
Implementing secure Software Development Life Cycle practices is important because developers cannot afford to release a product with security vulnerabilities. In order to protect the software and data from threats and attacks, it must be developed in a way that ensures security.
Another reason for it is that it is not an efficient approach to develop software without focusing on security and then testing and correcting it.
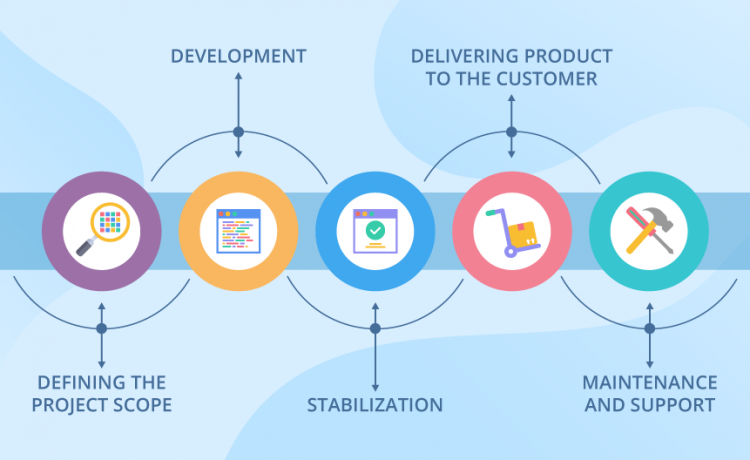
Phases of Secure SDLC
The whole concept of secure SDLC revolves around nipping the evil in the bud. The process prevents defects from being carried forward to the next phase of the software development life cycle. Here’s a sketch of the phases involved in Secure SDLC and the security measures implemented in each of them.
Requirements Phase of Secure SDLC
Along with the functional requirements of the software, the security requirements are also described at the start of secure SDLC. These requirements detail what is required of the developers to make the software inherently secure.
A detailed list of all the Security related Use Cases and Scenarios is compiled before the development starts. This is then used to create the security features and design security testing scenarios.
These requirements can look something like this:
- All gateways and entrance points must have authentication measures in place.
- The system must implement authentication through a secured login screen.
- All personal data must be encrypted at all times.
- More than one channel of authentication should be used for sensitive data transfer.
Planning Phase for Secure SDLC
The planning phase is the pivotal step in Secure SDLC. Planning can differ from case to case but here are some of the most fundamental things that must be taken care of:
- An experienced dedicated security team must be formed to overlook and direct all the security-related measures of the software in an impartial way. This team, preferably stationed outside the project management office, should consist of a security officer, security architects, and security testers. All of the team members must have clearly defined roles and responsibilities.
- Any ambiguities or escalations related to the security issues of the project must be handled by the product security officer. He is to be advised by the security team to make sure the right decisions are made.
- A security point of contact must be established to make sure that any changes made to the security of the product do not go unnoticed by the security team.
Architecture And Design Phase of SDLC
A detailed Product Security Risk Assessment must be performed during the design phase. This includes reviewing the program from a security point of view while it has not entered the coding stage. Any security risks must be eliminated before entering the next phase. In order to ensure security, all the assessments must be carried out according to industry standards.
The things that must be taken care of during this phase include but are not limited to:
- Reviewing all the features, requirements, user stories, and design documents according to the details shared by the project team. In case of the absence of any of the required documents, everything must clearly be discussed by the project team members.
- Any gaps in the security requirements of the program must be identified and evaluated against industry standards being used. If needed, threat models can be created according to the identified gaps.
- The gaps with sufficient security risks should be listed and viable mitigation is suggested for them.
Development Phase of SDLC
This is the actual “development” of the software. After a secure layout of the application has been prepared, the developers have to write the code in a way that is in line with the security guidelines. This includes:
- Use of open-source components with no known vulnerabilities.
- Using the agreed security measures throughout the development of the software.
- Cold-testing the code to expose and mitigate any vulnerability in the code.
Some testing is also done in the phase. This can include things like ensuring that sensitive data is not transmitted as plain text.
Implementation Phase of SDLC
Once the software has been developed, the next step is dynamic code analysis. This is a form of application security testing, also known as Open Web Application Project (OWASP) testing.
Before the solution is implemented in real life the Vulnerability Analysis and Penetration Testing are performed. The versions of the software on which this check is performed are called test builds. The main things to be noted about this include:
- Tools like HP WebInspect, ZAP, Burp Suite, and SOAP are used to check the vulnerabilities of the software against various vulnerability databases.
- This whole phase is a mixture of automation and manual testing.
- This process is performed in an independent environment not linked to the development environment to ensure close-to-reality testing scenarios.
- Any vulnerability found in this phase is mitigated before releasing the software.
- Common and typical threats are identified during this phase and steps are taken to prevent them.
Conclusion
As our dependence on software continues to increase, it is important to make them secure for the users. To make sure that software and applications are up to the mark in security, Secure SDLC practices are adopted. The ultimate goal always is to create software solutions that are invulnerable.
THE secure SDLC process has five phases starting from the gathering of the requirements to the pre-deployment testing. The focus is to mitigate threats and vulnerabilities at every step so that they are not carried forward to the next step.
